What is Emotet?
Emotet is a malware infection that uses spam emails containing Word or Excel documents, that when opened and downloaded, installs an Emotet Trojan that develops into a ransomware attack on your company network.

What is the Attachment?
Businesses need to be aware of the Emotet botnet spam email that resurfaced on the 14th of October this year and is landing in company inboxes worldwide. The email includes a deceiving attachment that claims to be a message from ‘Windows Update’ demanding you to upgrade Microsoft Word.
How do I identify it in my Inbox?
This is where it gets tricky. As with most spam emails, it’s not always easy to identify the sender or content (unless there are some obvious spelling mistakes). The content within the Emotet botnet emails in this case can vary but are likely to be disguised as COVID-19 Information, President Trump’s Health Updates, Company Invoices, Shipping information, C.V’s, or Purchase Orders.

When opened, these attachments will prompt a user to 'Enable Content' so that malicious macros will run to install the Emotet malware on a victim's computer. It will ask the user to update Microsoft Word by clicking on an Enable Editing or Enable Content button, which downloads and installs the malware on your device.
What will happen if I open the attachment?
Emotet is targeting users on a global scale and is especially risky because of the malicious malware it installs on your devices including Trickbot and QBot that can steal your stored passwords, financial information, and company-wide data usually leading to ransomware attacks.
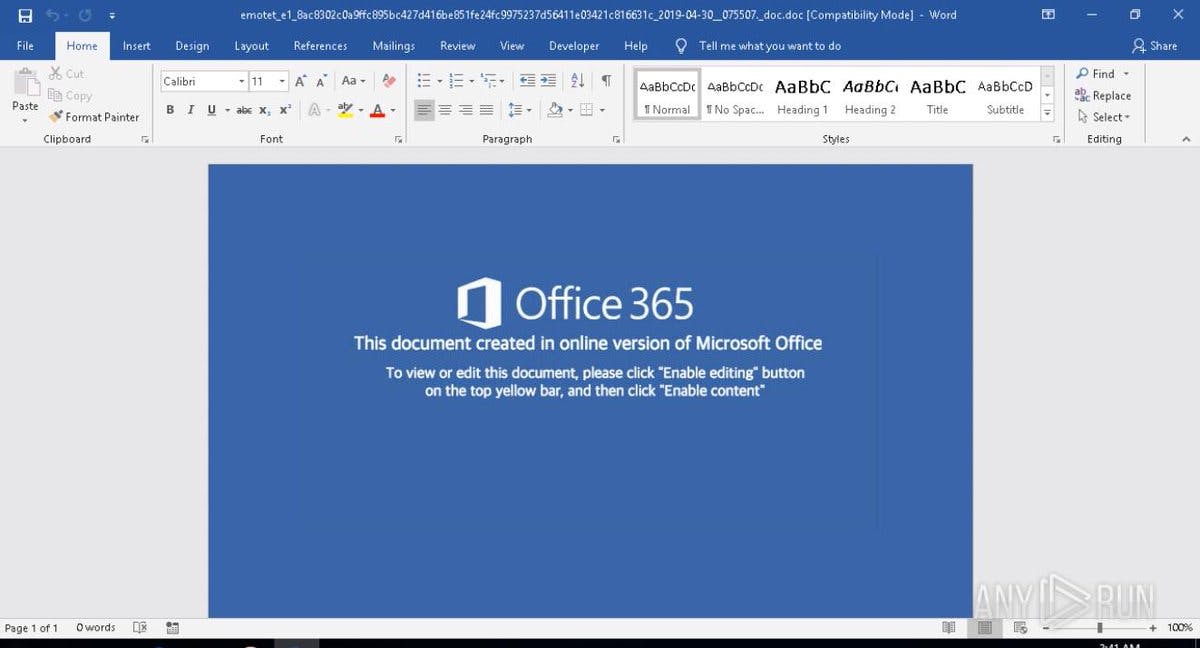
What should I do if I notice a suspicious email?
Do not open it. Always contact your IT services department or MSP if you suspect an email has been sent to you from a suspicious source, as it is likely bad news! Make sure that you have everything you need for the security of your networks and systems, and ensure you have a Cyber Resilience Framework in place to avoid such attacks.
If you suspect your business needs to implement an up-to-date cyber security plan, get in touch with us through our contact page, or visit our Cyber Essentials for more info.
Related posts
Visit blog
ERP System Implementation: The Complete Strategic Guide to Building a Smarter Business
Discover how to plan and implement an ERP system successfully. Learn best practices, avoid pitfalls, and explore Dynamics 365 Business Central with NetMonkeys
Navigating the ERP Journey: The Essential Guide to Implementation and Cost in the UK (2025)
Choosing the right business management software is a high-stakes strategic decision, and the Microsoft Dynamics ecosystem frequently emerges at the forefront of the conversation.

Decoding Microsoft Dynamics: What is the Fundamental Difference Between Dynamics 365 and Business Central?
Choosing the right business management software is a high-stakes strategic decision, and the Microsoft Dynamics ecosystem frequently emerges at the forefront of the conversation.
